Security
Security
Institut Pasteur targeted by a phishing campaign – be on your guard!
The Institut Pasteur was targeted by a phishing campaign sent to several email addresses during the week of January 13.
Dropbox was used to share a malicious file.
A similar attack could happen again and may affect other file-transfer systems (such as WeTransfer, TempSend, TransferNow and Bynder).
To prevent such an attack, here are some key things to watch out for, as illustrated with the Dropbox case:
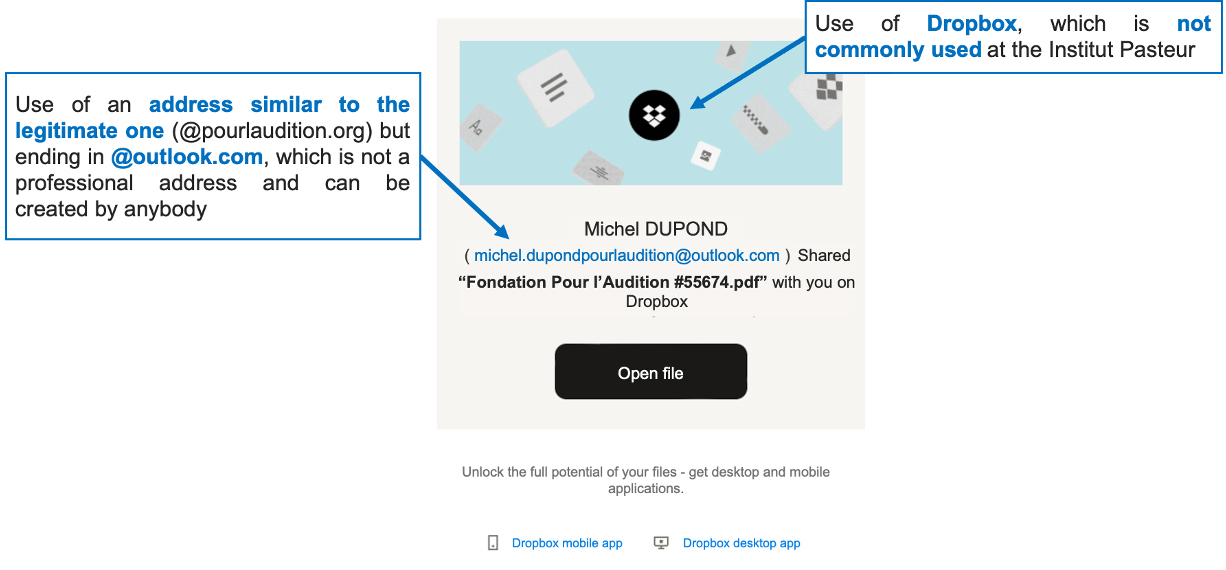
In the email received:
In the shared file, accessible on the Dropbox site, which is like the file below:
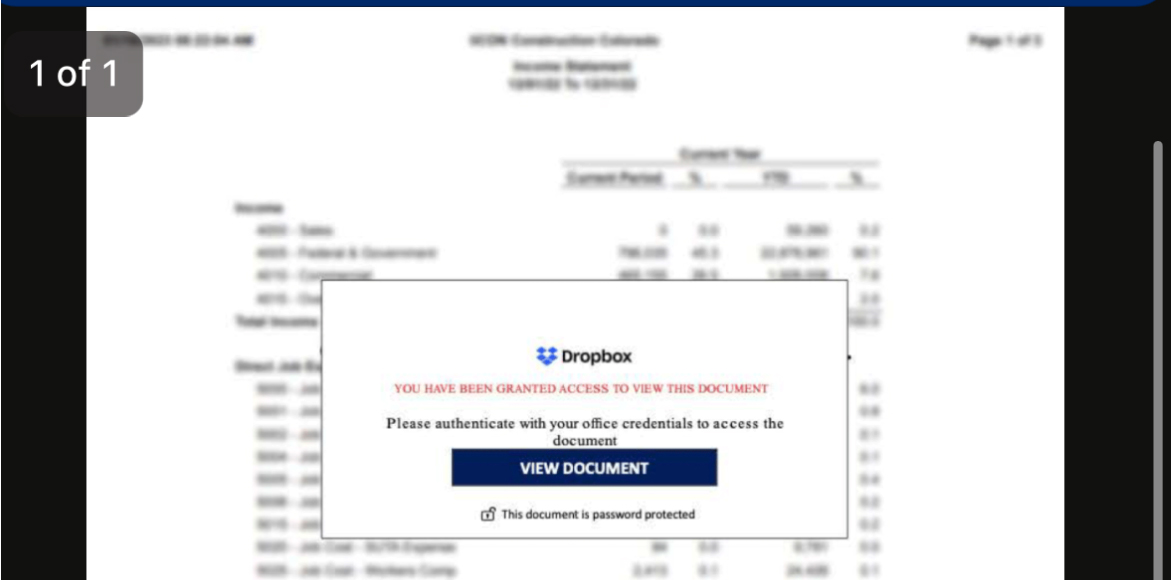
You are asked to log in to view the content: this is unusual – when you click on the link, you arrive on the attacker's website and they can steal the login and password that you enter!
To prevent this type of attack:
• Use the tools provided by the Institut Pasteur's Information Systems Department (NextCloud or Sharepoint if your data is not sensitive);
• Pay attention to the senders of emails that you receive and to contacts sharing information;
• If you're not sure:
- Confirm that the email is legitimate by contacting the sender via your usual means of communication with them: that is what the Institut Pasteur employee did for the Dropbox case, by contacting the legitimate address that had been hacked, and this meant that the Information Systems Security (SSI) team could be alerted and deal with the attack more quickly.
- Notify the SSI team of any suspicious emails so they can be analyzed (procedure here).
The SSI team would like to thank you for contributing to the security of our information systems.